Single Sign On Configurations
Single sign-on (SSO) is an identification method that enables users to log in to multiple applications and websites with one set of credentials. SSO streamlines the authentication process for users.
Configure CircuitVerse with SAML based SSO using Okta
Step 1: Configure Okta
This guide provides step-by-step instructions for setting up SAML-based Single Sign-On (SSO) for CircuitVerse using Okta as the Identity Provider (IdP).
-
Log in to your Okta Admin Dashboard.
-
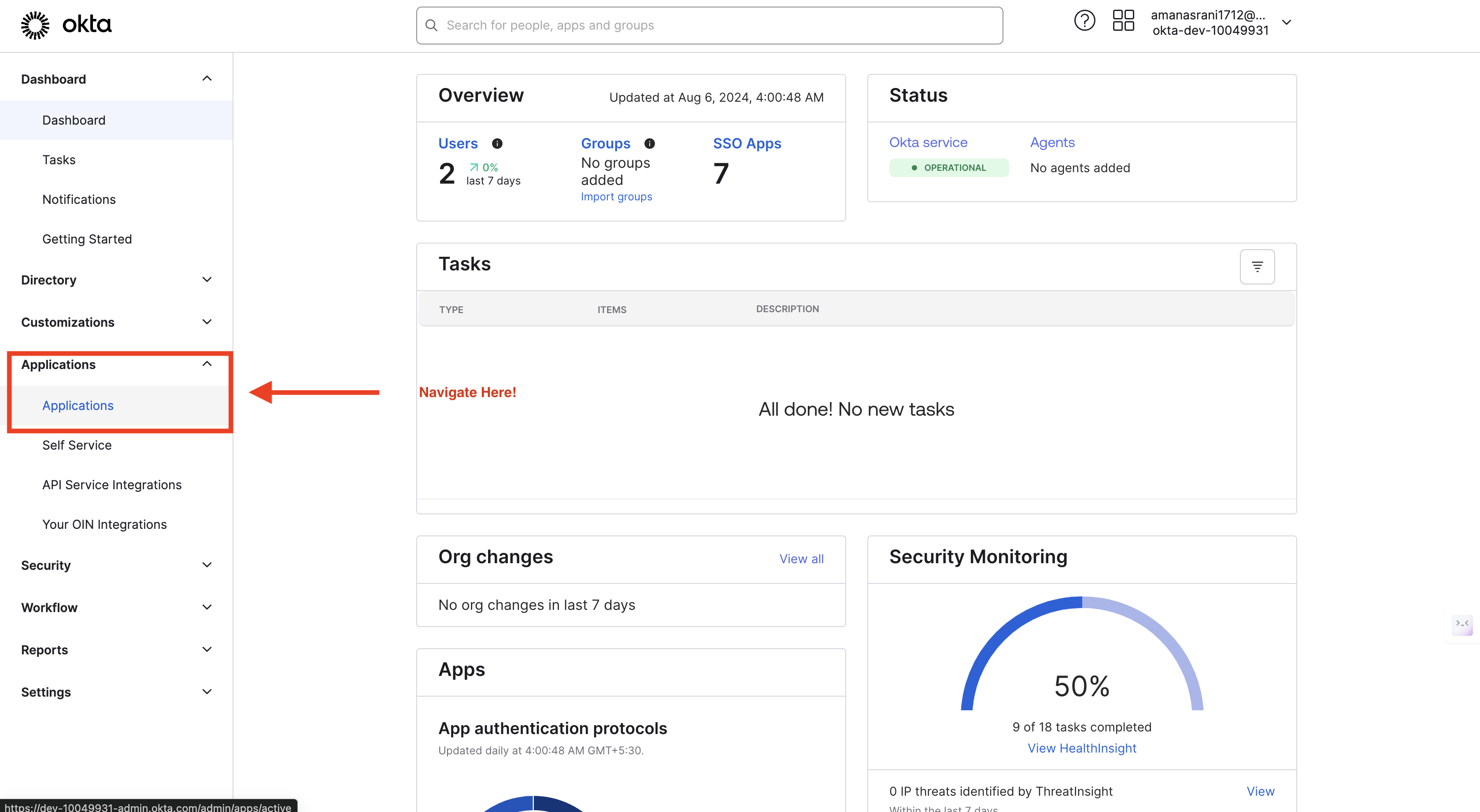
Navigate to "Applications" > "Applications" in the main menu.
-
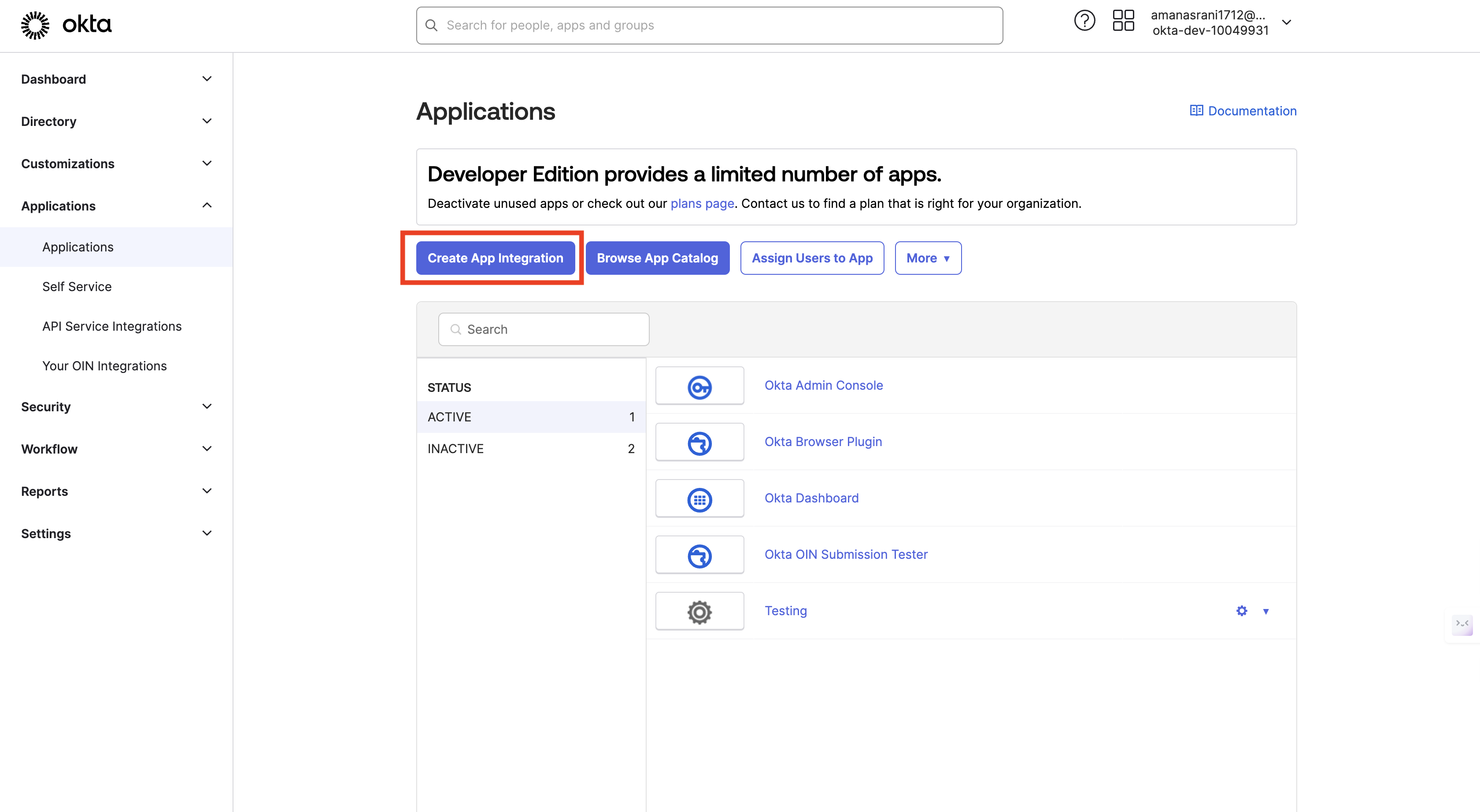
Click on "Create App Integration".
-
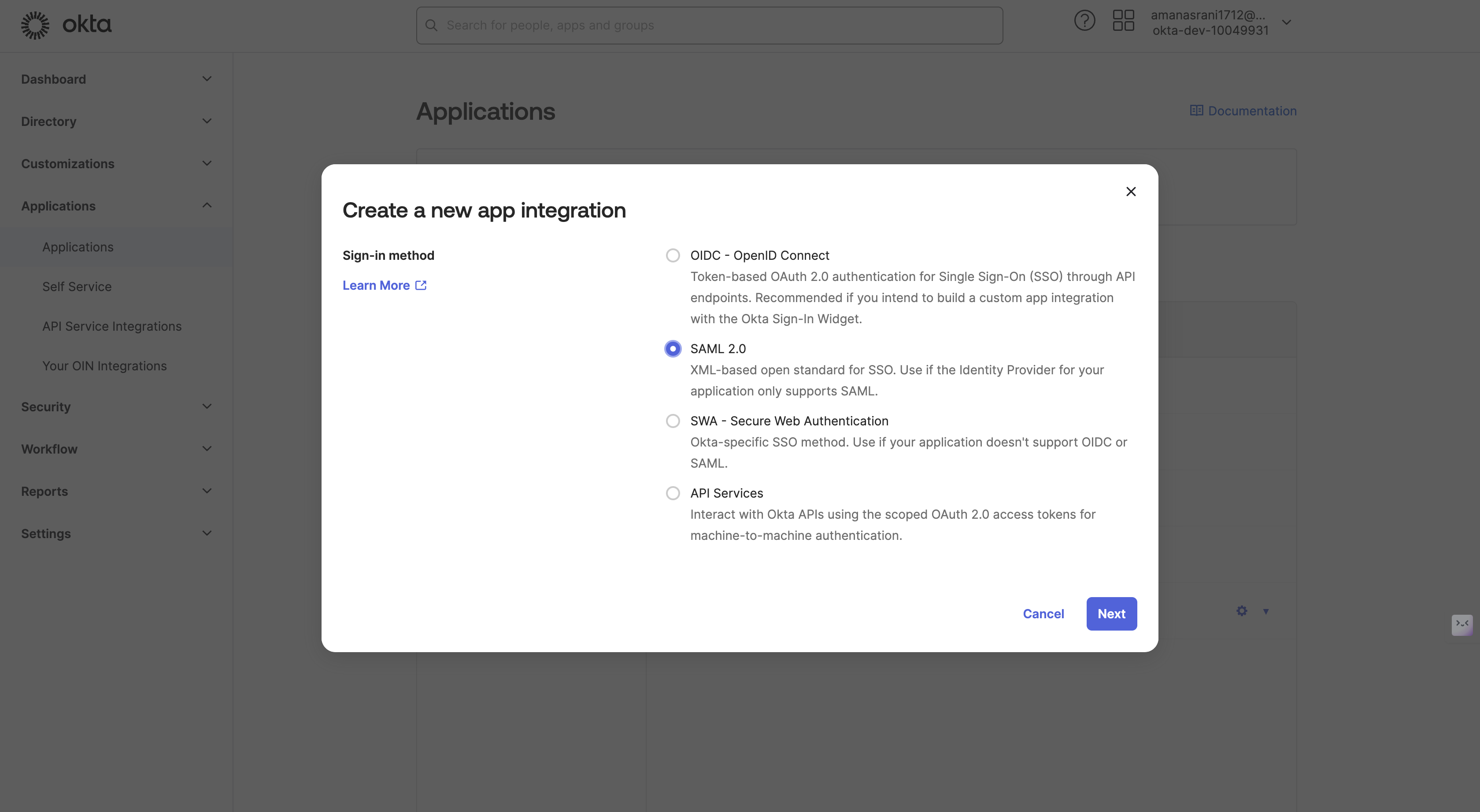
Select "SAML 2.0" as the Sign-on method and click "Next".
-
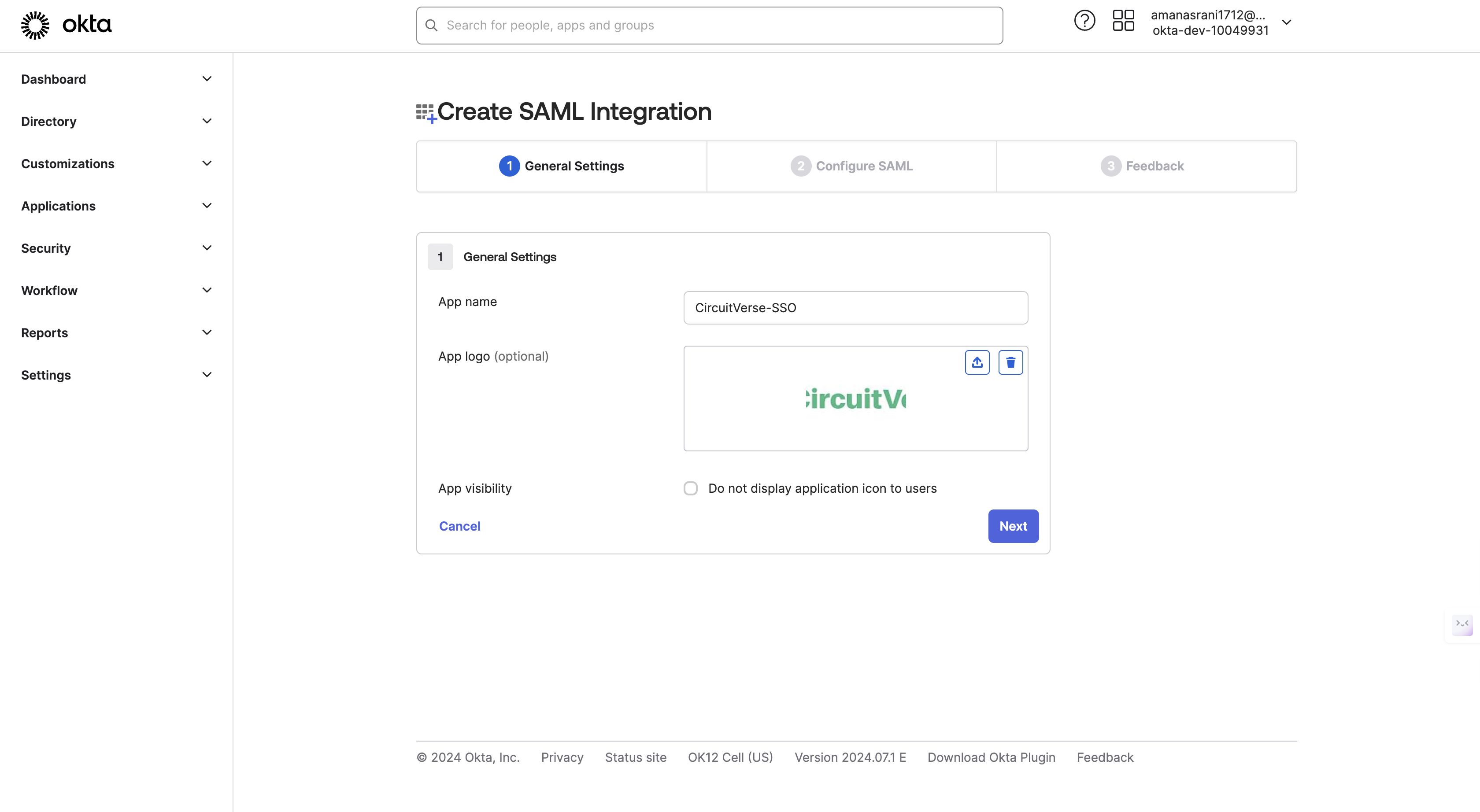
Fill in the following details for your CircuitVerse app:
- App name: "CircuitVerse" (or your preferred name)
- App logo: (Optional) Upload CircuitVerse logo
-
In the "SAML Settings" section, configure the following:
- Single sign on URL
https://your-circuitverse-domain.com/users/saml/auth - Audience URI (SP Entity ID):
https://your-circuitverse-domain.com/users/saml/metadata - Name ID format:
Transient - Application username:
Email
In the image below, the domain
https://localhost:3000is shown as an example. You should replace it with your own domain.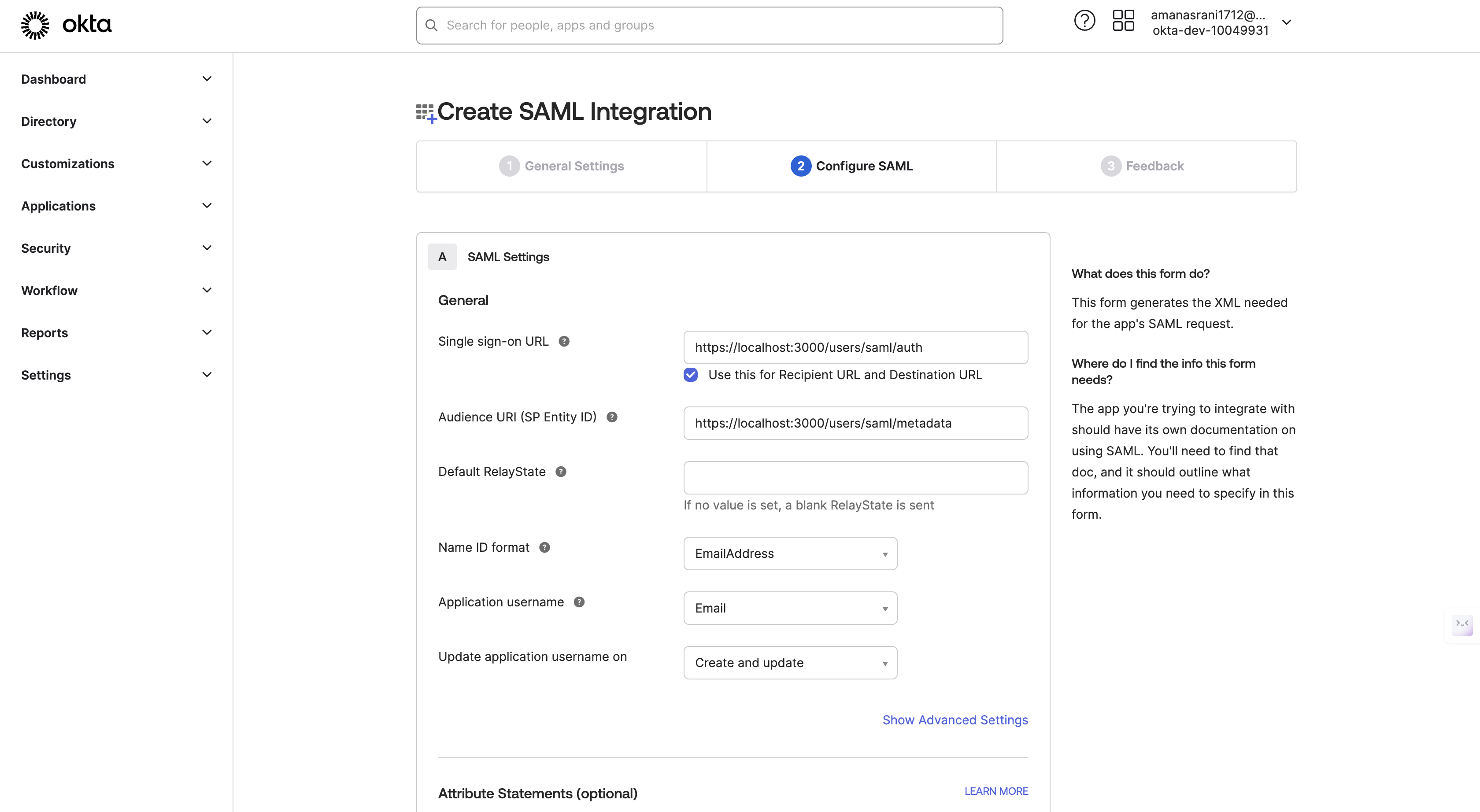
- Single sign on URL
-
Click "Next" and select "I'm an Okta customer adding an internal app".
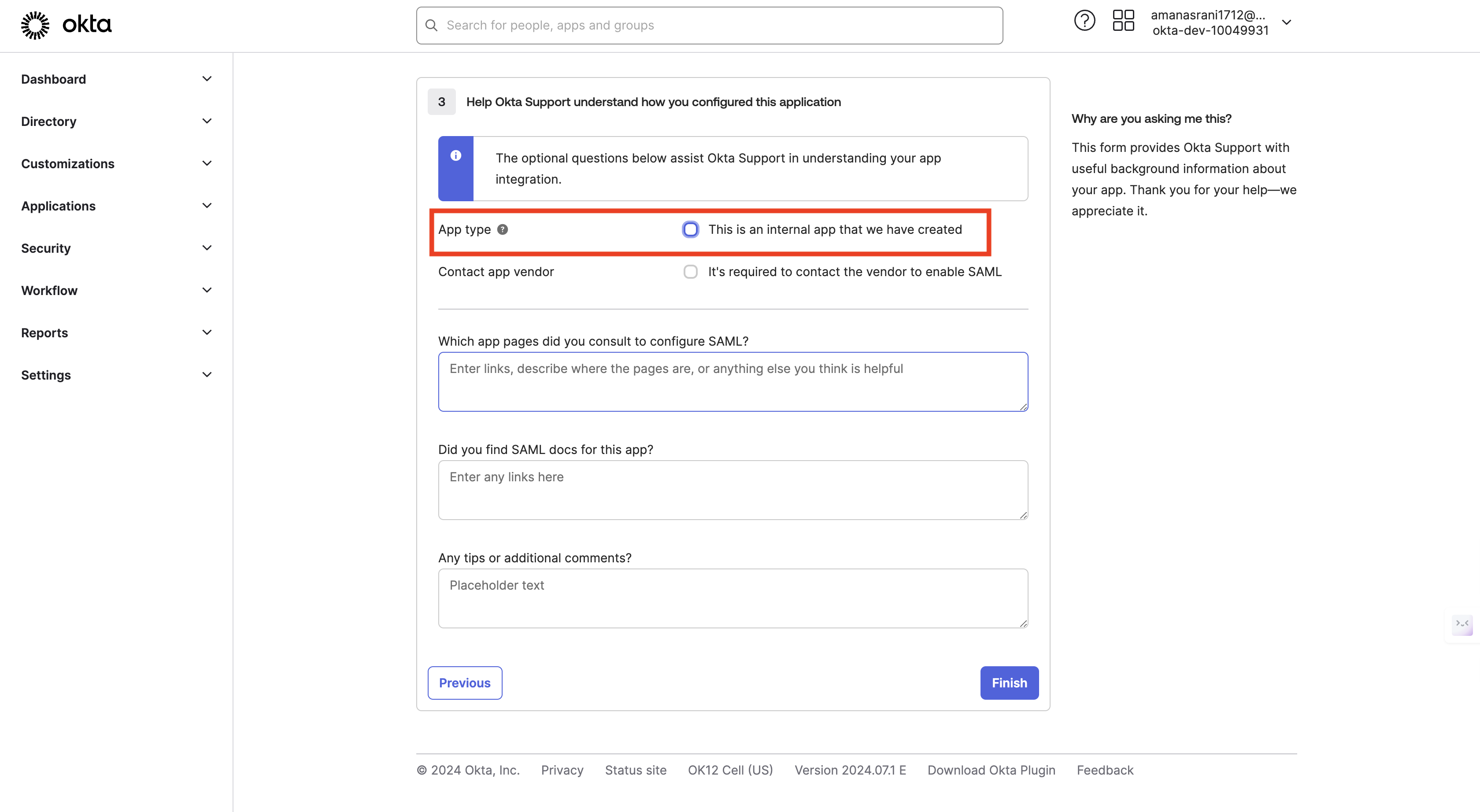
-
Click "Finish" to create the application.
-
In the "Sign On" tab of your new application, find the "Identity Provider metadata" or "View Setup Instructions" to obtain the following information:
- Identity Provider Single Sign-On URL
- Identity Provider Issuer
- Certificate FingerPrint
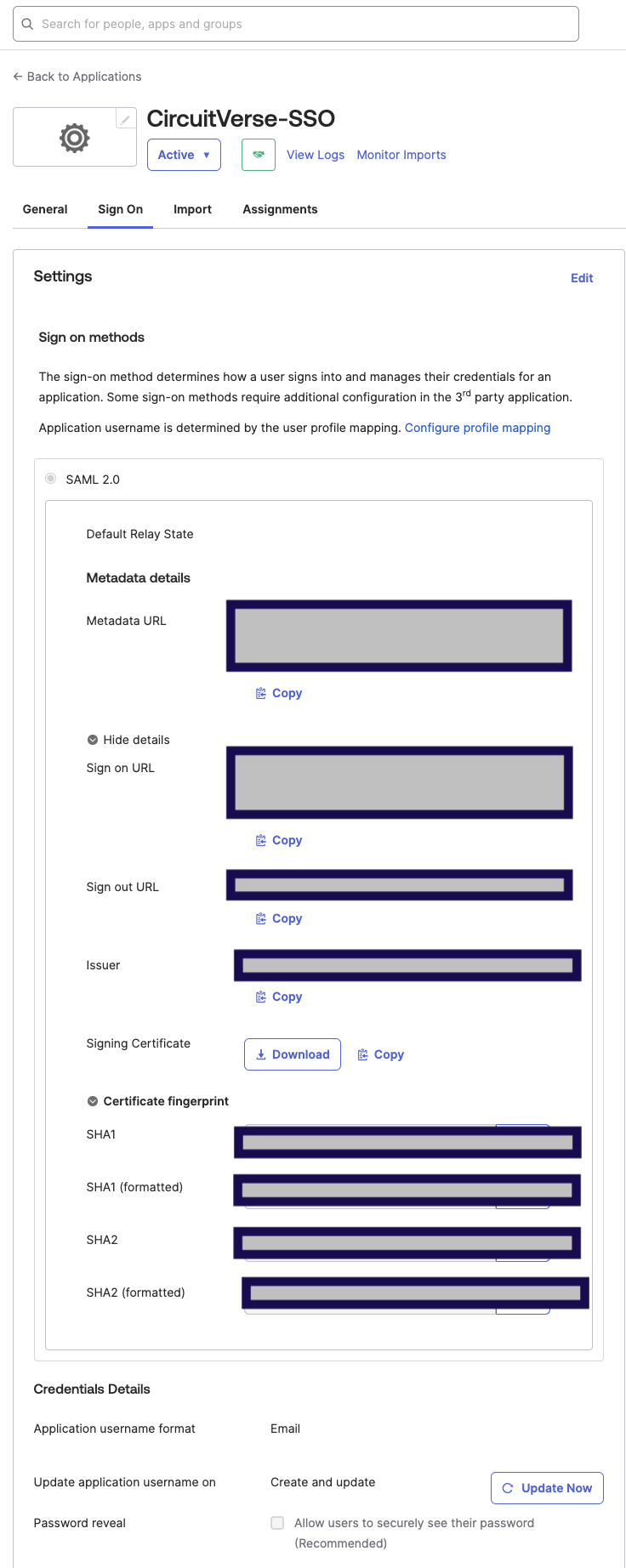
-
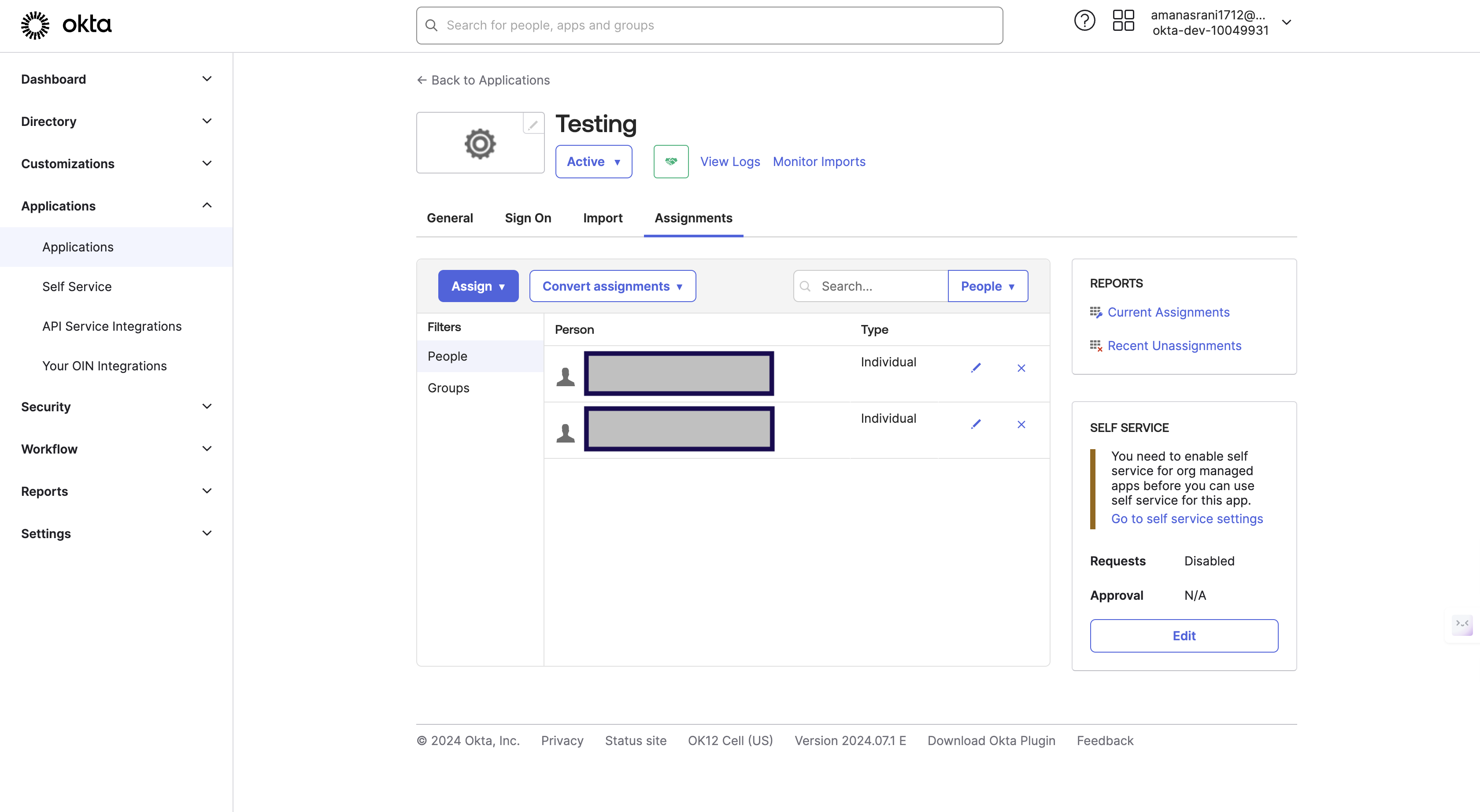
You can add users and groups by navigate to Assignment > Assign > Assign to People / Assign to Groups
Step 2: Configure CircuitVerse
- Create a
.envfile and add the following credentials obtained from configuring Okta:IDP_SSO_URL=<sso-idp-url>IDP_FINGERPRINT=<sso-idp-fingerprint-certificate>
Step 3: Enable SSO in CircuitVerse UI
- Enable the sso_integration feature flag using Flipper (if not already enabled).
- Verify that the SSO login option appears on the login page.
Step 4: Test the Integration
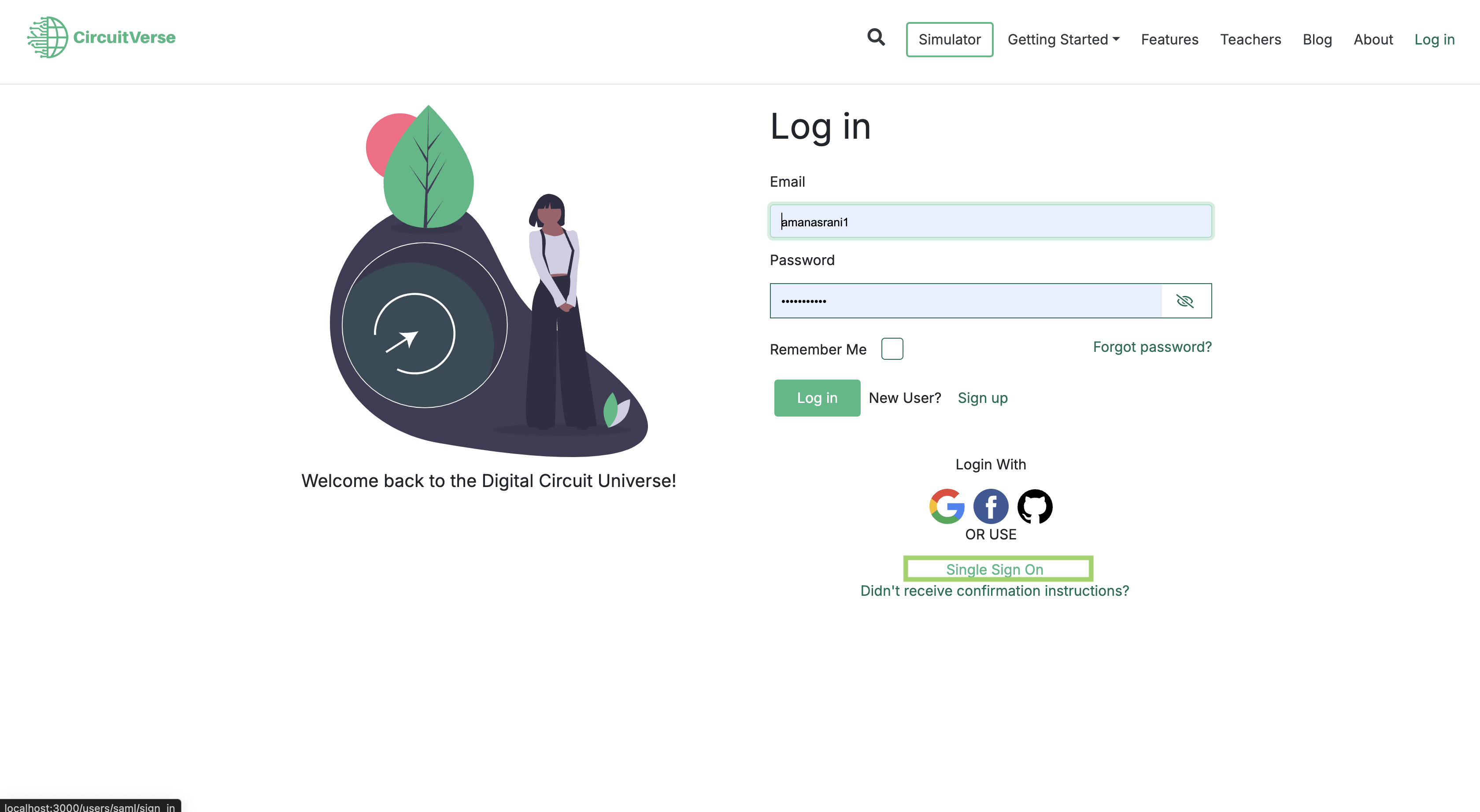
- Log out of CircuitVerse.
- Click on the "Login with SSO" button on the CircuitVerse login page.
- You should be redirected to the Okta login page.
- Enter your Okta credentials.
- After successful authentication, you should be redirected back to CircuitVerse and logged in.
Configure CircuitVerse with SAML based SSO using Keycloak
This guide provides step-by-step instructions for setting up SAML-based Single Sign-On (SSO) for CircuitVerse using Keycloak as the Identity Provider (IdP).
Step 1: Configure Keycloak
-
Go to the Keycloak Admin console UI and sign in as an administrator
-
Select or create a realm for CircuitVerse.
-
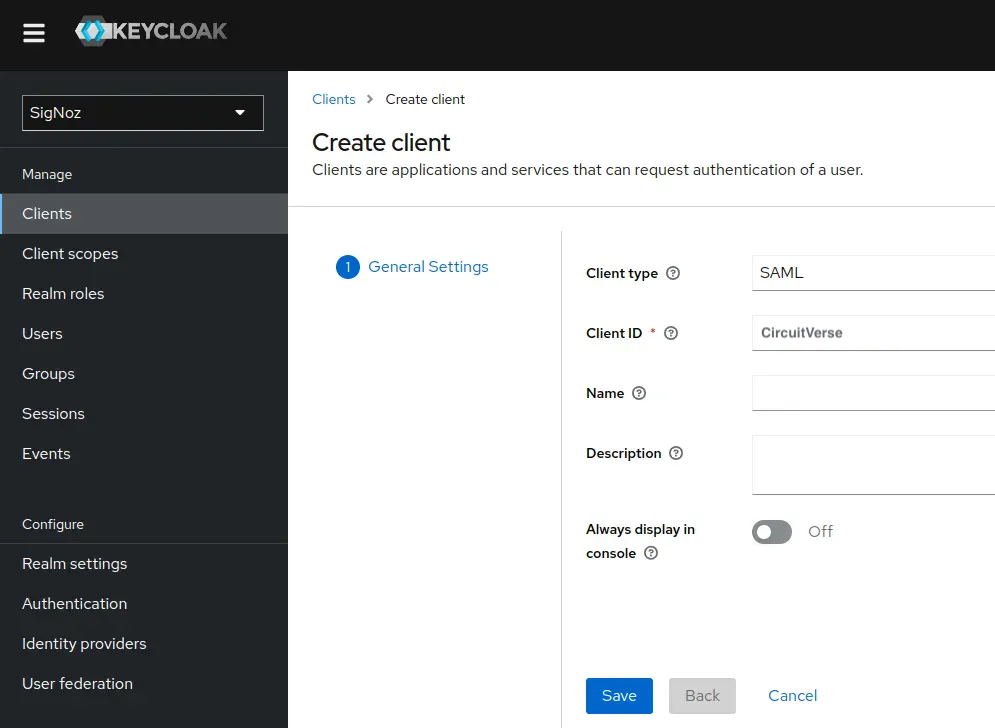
In the left sidebar, click on "Clients" and then click "Create" to add a new client.
-
Client ID: CircuitVerse (or your preferred name)
-
Client Type: Select
SAML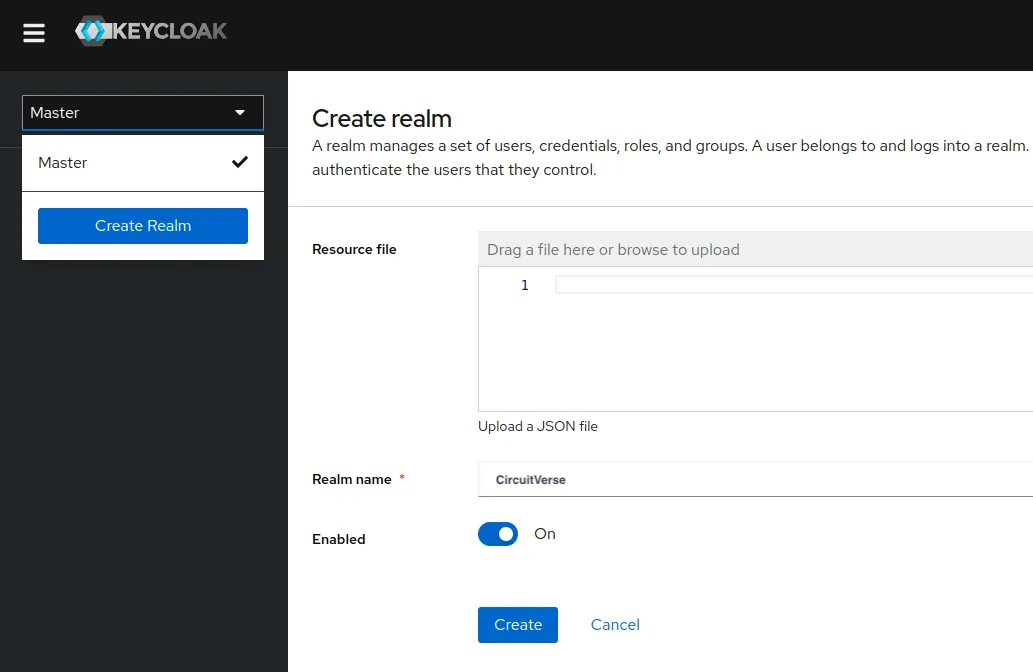
-
-
Click "Save" to create the client.
-
In the client settings, configure the following:
-
Valid Redirect URIs: https://your-circuitverse-domain.com/
-
Base URL: https://your-circuitverse-domain.com
-
Master SAML Processing URL: https://your-circuitverse-domain.com/users/saml/auth
In the image below, the domain
https://localhost:3000is shown as an example. You should replace it with your own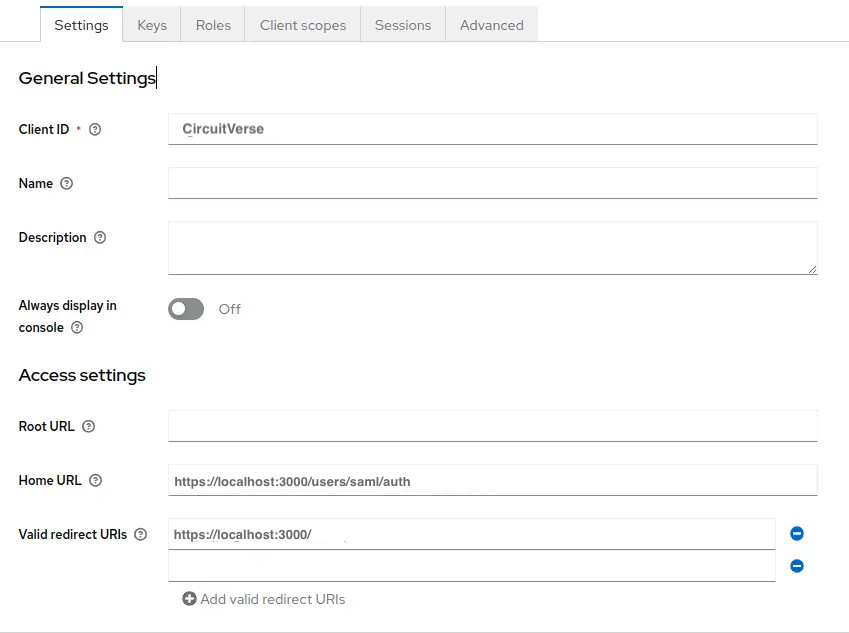
-
-
Go to Clients > Client scopes, and select
{Your-realm-name}and add predefined mappers such asEmail -
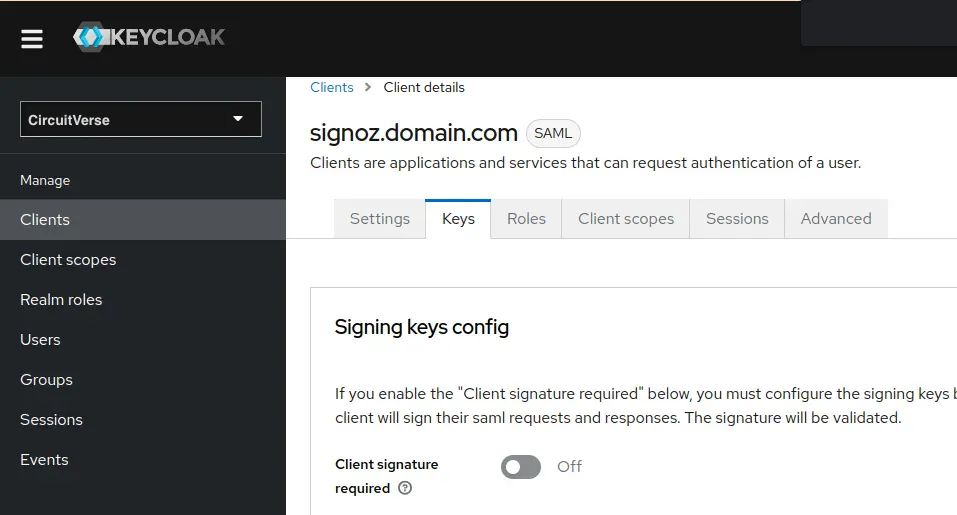
Go to Clients > Keys, and turn off the Client signature required option from signing keys config
-
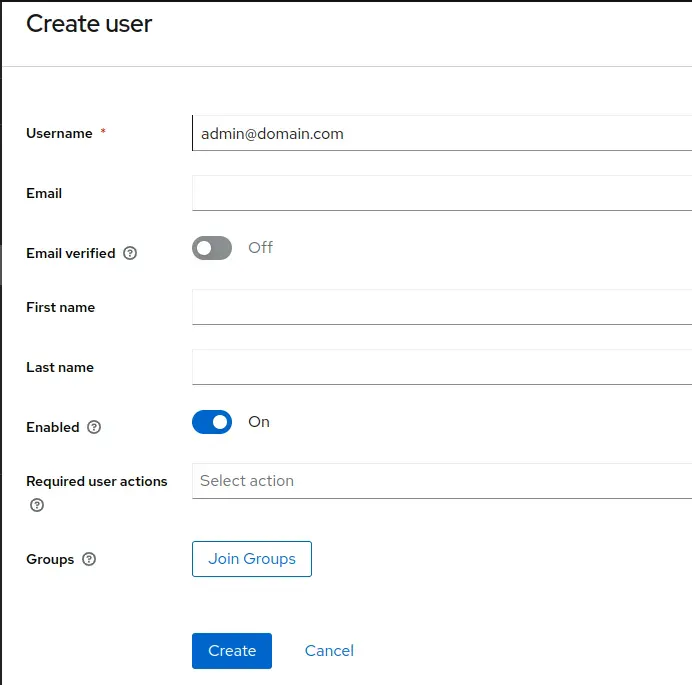
Create new user which is to be used for login. Be sure to include email id in username and email fields
Step 2: Extract Keycloak SAML Credentials
To get the required credentials for CircuitVerse (IDP_SSO_URL and IDP_FINGERPRINT), follow these steps:
- Open the downloaded XML file in a text editor.
- Find the "SingleSignOnService" tag. The "Location" attribute of this tag is your
IDP_SSO_URL. - From this XML file make note of
SAML entity idandSAML X.509 certificate
Step 3: Configure CircuitVerse
- Create a
.envfile and add the following credentials obtained from configuring Okta:IDP_SSO_URL=<sso-idp-url>IDP_FINGERPRINT=<sso-idp-fingerprint-certificate>
Step 4: Enable SSO in CircuitVerse UI
- Enable the sso_integration feature flag using Flipper (if not already enabled).
- Verify that the SSO login option appears on the login page.

Step 5: Test the Integration
- Log out of CircuitVerse.
- Click on the "Login with SSO" button on the CircuitVerse login page.
- You should be redirected to the Keycloak login page.
- Enter your KeyCloak credentials.
- After successful authentication, you should be redirected back to CircuitVerse and logged in.